Discussion
Home ‣ Networking ‣ Subnetting See What Others Are Saying!
- Question
A network administrator is connecting hosts A and B directly through their Ethernet interfaces, as shown in the illustration. Ping attempts between the hosts are unsuccessful. What can be done to provide connectivity between the hosts?
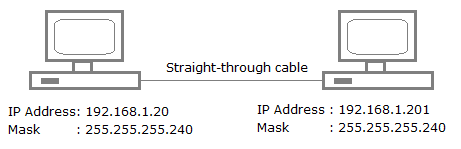
- A crossover cable should be used in place of the straight-through cable.
- A rollover cable should be used in place of the straight-through cable.
- The subnet masks should be set to 255.255.255.192.
- A default gateway needs to be set on each host.
- The subnet masks should be set to 255.255.255.0.
Options- A. 1 only
- B. 2 only
- C. 3 and 4 only
- D. 1 and 5 only
- E. 2 and 5 only
- Correct Answer
- 1 and 5 only
ExplanationFirst, if you have two hosts directly connected, as shown in the graphic, then you need a crossover cable. A straight-through cable won't work. Second, the hosts have different masks, which puts them in different subnets. The easy solution is just to set both masks to 255.255.255.0 (/24). - 1. Which class of IP address has the most host addresses available by default?
Options- A. A
- B. B
- C. C
- D. A and B Discuss
- 2. How many non-overlapping channels are available with 802.11a?
Options- A. 3
- B. 12
- C. 23
- D. 40 Discuss
- 3. You have the following routing table. Which of the following networks will not be placed in the neighbor routing table?
R 192.168.30.0/24 [120/1] via 192.168.40.1, 00:00:12, Serial0 C 192.168.40.0/24 is directly connected, Serial0 172.16.0.0/24 is subnetted, 1 subnets C 172.16.30.0 is directly connected, Loopback0 R 192.168.20.0/24 [120/1] via 192.168.40.1, 00:00:12, Serial0 R 10.0.0.0/8 [120/15] via 192.168.40.1, 00:00:07, Serial0 C 192.168.50.0/24 is directly connected, Ethernet0
Options- A. 172.16.30.0
- B. 192.168.30.0
- C. 10.0.0.0
- D. All of them will be placed in the neighbor routing table. Discuss
- 4. You have created a named access list called Blocksales. Which of the following is a valid command for applying this to packets trying to enter interface s0 of your router?
Options- A. (config)# ip access-group 110 in
- B. (config-if)# ip access-group 110 in
- C. (config-if)# ip access-group Blocksales in
- D. (config-if)# blocksales ip access-list in Discuss
- 5. What multicast addresses does RIPng use?
Options- A. FF02::A
- B. FF02::9
- C. FF02::5
- D. FF02::6 Discuss
- 6. What is the maximum distance running the lowest data rate for 802.11a?
Options- A. About 100 feet
- B. About 175 feet
- C. About 300 feet
- D. About 350 feet Discuss
- 7. Which of the following is considered to be the destination host before translation?
Options- A. Inside local
- B. Outside local
- C. Inside global
- D. Outside global Discuss
- 8. Which router command allows you to view the entire contents of all access lists?
Options- A. show all access-lists
- B. show access-lists
- C. show ip interface
- D. show interface Discuss
- 9. Which layer 4 protocol is used for a Telnet connection?
Options- A. IP
- B. TCP
- C. TCP/IP
- D. UDP Discuss
- 10. What protocol does PPP use to identify the Network layer protocol?
Options- A. NCP
- B. ISDN
- C. HDLC
- D. LCP Discuss
More questions
Correct Answer: A
Explanation:
Class A addressing provides 24 bits for host addressing.
Correct Answer: 12
Explanation:
The IEEE 802.11a standard provides up to 12 non-overlapping channels.
Correct Answer: 10.0.0.0
Explanation:
The network 10.0.0.0 cannot be placed in the next router's routing table because it already is at 15 hops. One more hop would make the route 16 hops, and that is not valid in RIP networking.
Correct Answer: (config-if)# ip access-group Blocksales in
Explanation:
Using a named access list just replaces the number used when applying the list to the router's interface.
ip access-group Blocksales in is correct.
Correct Answer: FF02::9
Explanation:
RIPng uses the multicast IPv6 address of
FF02::9. If you remember the multicast addresses for IPv4, the numbers at the end of each IPv6 address are the same.
Correct Answer: About 175 feet
Explanation:
The IEEE 802.11a standard's lowest data rate is 6Mbps, but it can run from a distance of about 175 feet.
Correct Answer: Outside local
Explanation:
The host on the global network before translation is considered to be an outside local host.
Correct Answer: show access-lists
Explanation:
To see the contents of all access lists, use the
show access-lists command.
Correct Answer: TCP
Explanation:
Although Telnet does use TCP and IP (TCP/IP), the question specifically asks about layer 4, and IP works at layer 3. Telnet uses TCP at layer 4.
Correct Answer: NCP
Explanation:
Network Control Protocol is used to help identify the Network layer protocol used in the packet.
Comments
There are no comments.Programming
Copyright ©CuriousTab. All rights reserved.
